Prepare for the unexpected with ethical disruption

ISO 9001 & 27001 certified

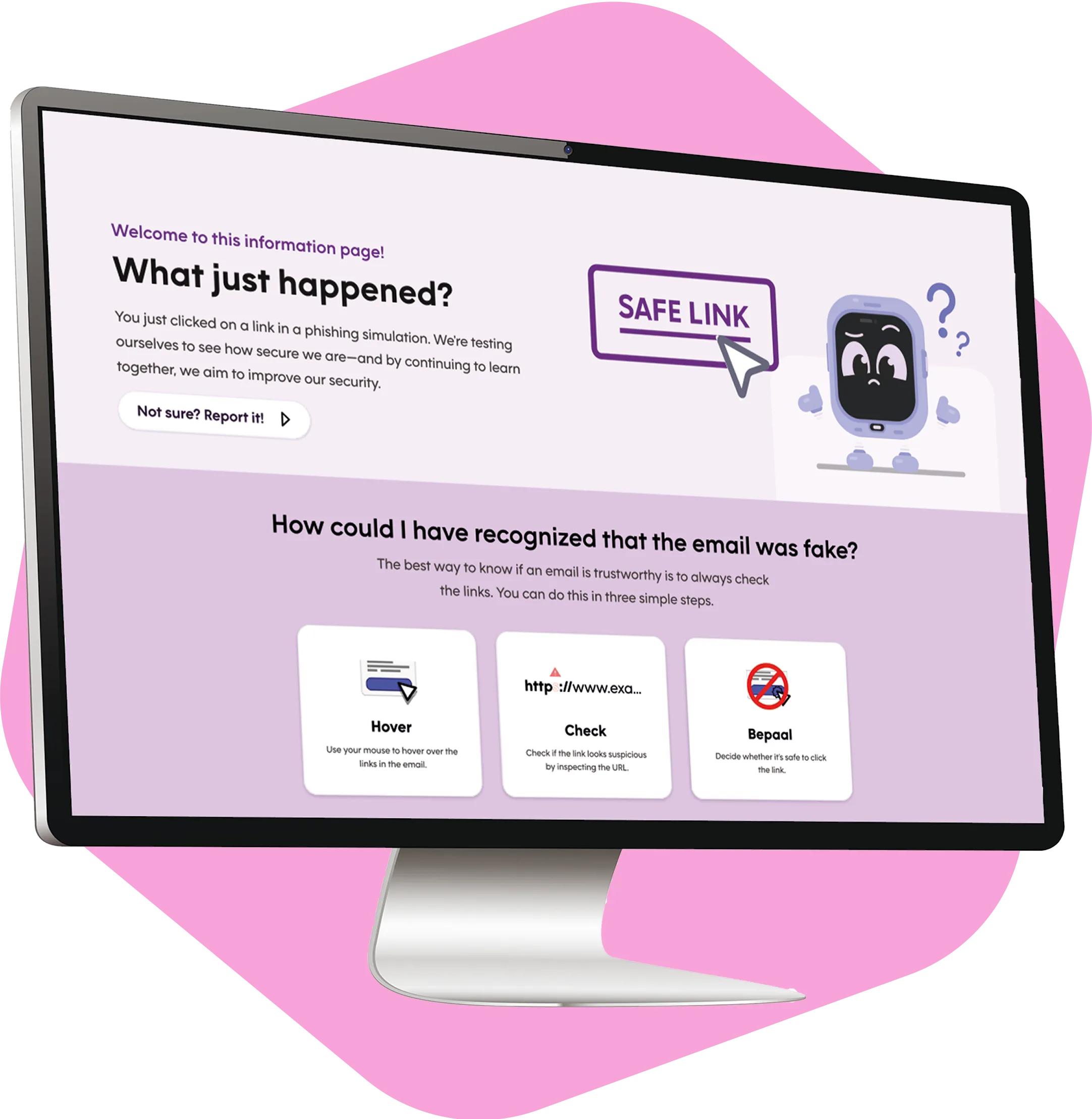
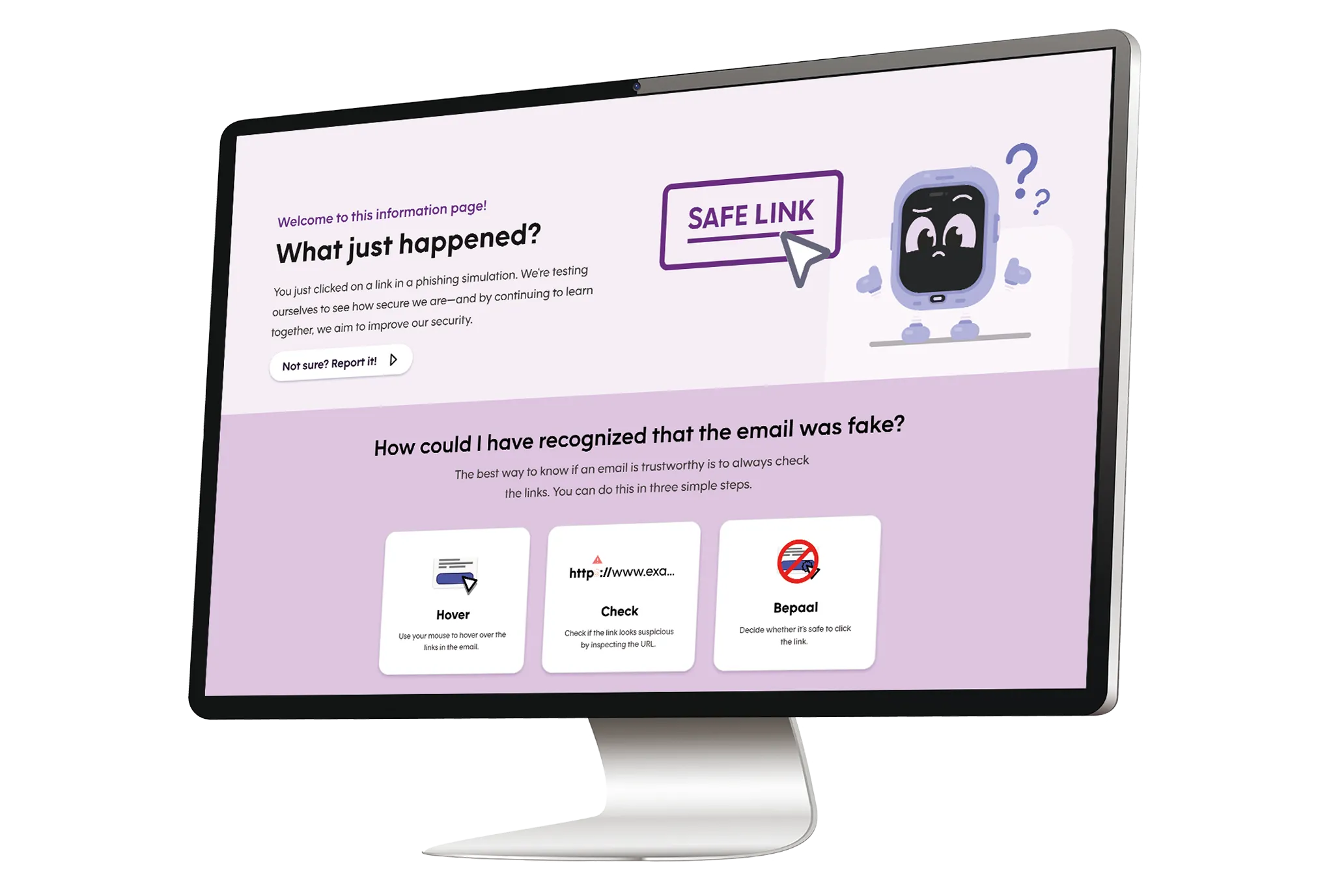
Initiate a reality check with interventions that shake assumptions and sharpen response.
Boost incident readiness with digital and real-world threat simulations
We transform theory into action with interactive, behavior-focused simulations that mirror real-world cyber risks.
Our promise:
From tabletop to USB drop
The best defense is lived experience. Our real-world simulations - whether phishing, vishing, or physical interventions - turn theory into action. By exposing vulnerabilities safely, we help employees build instincts to spot and stop threats. Adaptive, realistic, and disruptive simulations drive confidence, sharpen skills, and reduce risk for your organization.
Phishing simulations tailored
to your
organization
Adaptive strategies to
support all skill
levels
Behavioral metrics: click rates,
trends,
risk areas
Different simulation types
Positive reinforcement
for vigilant
employees
Multi-channel, evolving
simulations
across platforms
For example, with the phishing strategy we launched, the first round's score was pretty good; not perfect, but very telling. The second round was a bit lower, and the third and final round was somewhere in between. This really highlights that it needs ongoing focus, just like everything else. It's not about a single intervention, but about consistently working on it because cybercriminals are always refining their methods.
Bastiaan Mol
Information Security Officer at CIBG
(Executive agency of the Ministry of Health, Welfare and Sports)
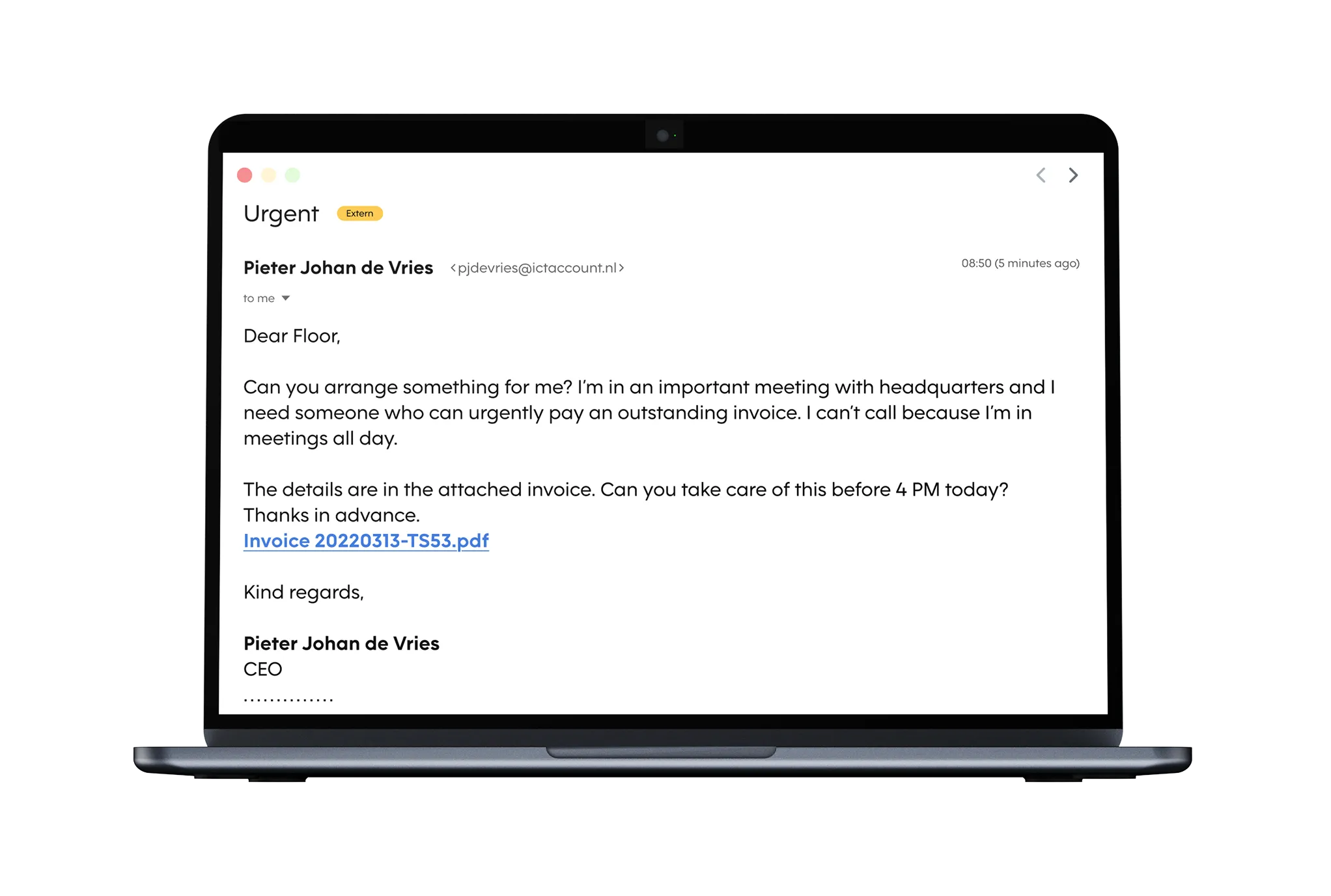
Deceptive emails
We simulate real-world email scams using various scam principles, using urgency, authority and impersonation. Each round is designed to monitor and enhance the learning curve, helping employees gradually improve their ability to spot suspicious emails over time.
Physical social engineering
Not all threats are digital. Unauthorized visitors can attempt to access sensitive areas by posing as employees, contractors, or inspectors. Our mystery guest assessments test physical security awareness and teach employees how to spot and challenge suspicious individuals.

Engaging scams
Some phishing attacks go beyond links—attackers pose as executives, suppliers, or IT staff to engage in conversation and extract sensitive information. Our simulations test employee responses and provide real-time feedback to strengthen awareness.
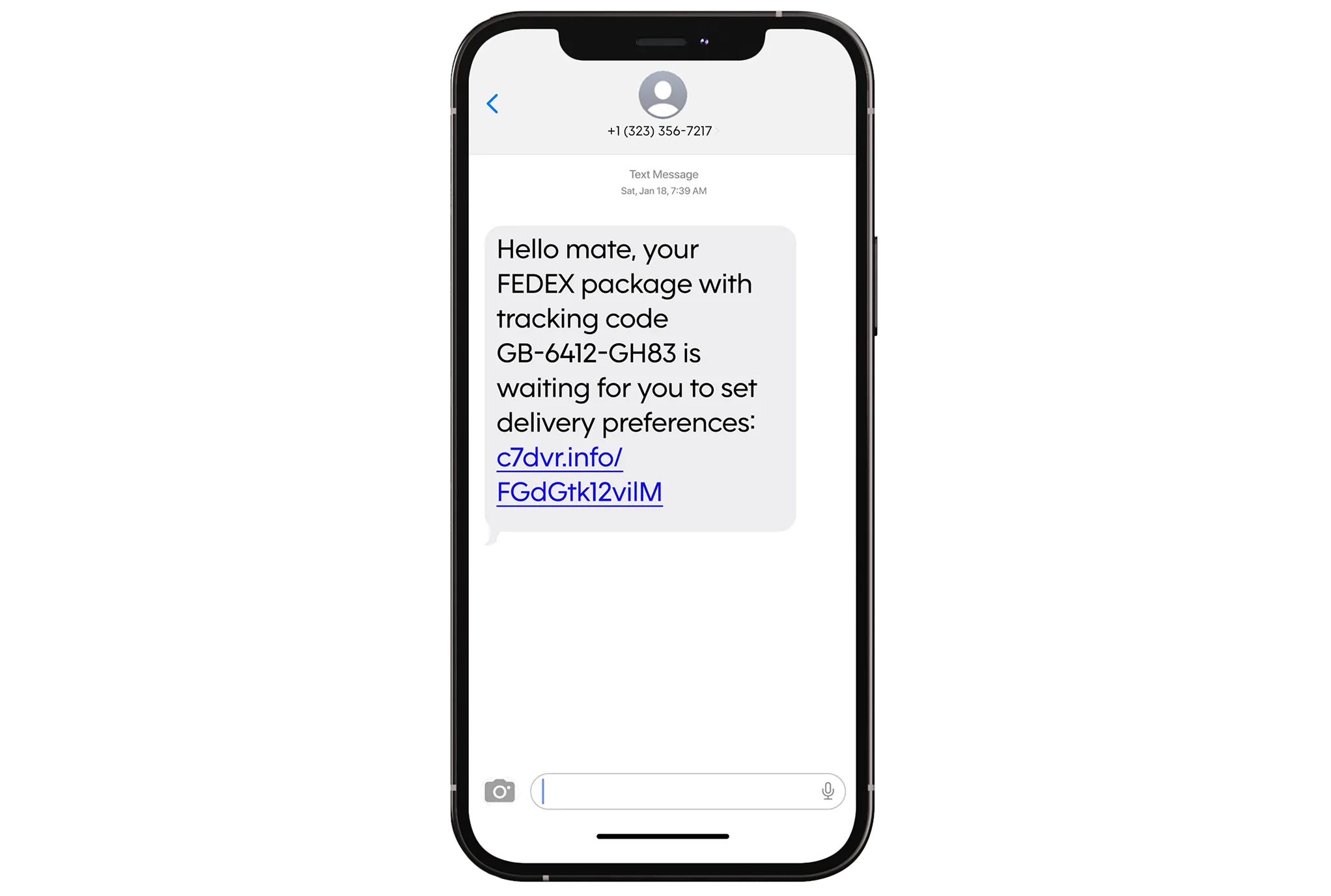
Mobile threats
Cybercriminals use fake SMS, WhatsApp or Signal messages from banks, delivery services, or internal teams to trick employees into clicking malicious links. Our simulations train employees to verify senders and respond cautiously to unexpected messages.
Deceptive calls
Attackers impersonate trusted contacts over the phone to gain access to confidential information. We simulate real-world vishing scenarios, helping employees recognize red flags and respond securely.

Strategy & impact
Every answer you need
Our adaptive training strategy tailors simulations and follow-up learning based on individual behaviors. Frequent clickers receive additional simulations and interactive training, while vigilant employees receive positive reinforcement to encourage continued awareness.
Yes. We design phishing scenarios that mirror real-world attacks and can be tailored to your industry, company culture, and the specific types of threats your employees are most likely to encounter.
Our intuitive dashboard provides key metrics including click rates per campaign, department, and template, as well as trend analysis over time. This allows you to track progress, identify areas needing improvement, and measure the overall impact of the training.
Absolutely. The simulations are designed to complement and enhance existing security awareness initiatives, providing hands-on experience and behavioral insights that can inform broader training and policy efforts.
We prioritize privacy and security. All data is stored securely in Europe under GDPR compliance, and we maintain transparency about how data is used. Our processes are designed with privacy and security built in.

Tom van Ruitenbeek
Social Engineering Expert
Need help finding what you're looking for?
Contact our client
support experts!